Local Attack is a popular method used to target websites on the same server by using exploit code known as shells. These shells allow attackers to access sensitive information like email and database details. To limit Local Attack in WordPress, steps include hiding wp-config.php, changing database prefixes, security keys, and file editing permissions. Additionally, securing wp-config.php with .htaccess, protecting the wp-content folder, locking the wp-admin path, and using malware scanning plugins are recommended. Choosing a reputable hosting provider that supports Local Attack restrictions is also crucial for ensuring website security.
Local attacks are a common method used to target websites on the same server. Attackers use exploit code written in languages like PHP, ASP.Net, and Python to upload shells onto hosting accounts. These shells allow attackers to access sensitive information such as emails and database details easily. This article will guide you on how to limit local attacks in WordPress effectively.
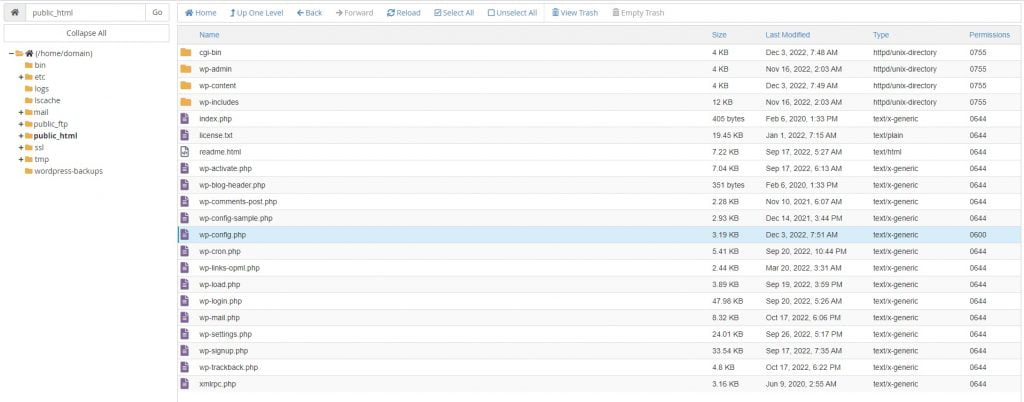
Hide wp-config.php file
To hide the wp-config.php file, move it out of the public_html folder. Create a new folder parallel to public_html, upload the file there, and edit the wp-config.php file in public_html accordingly.
Change database prefix
Changing the default database prefix "wp_" in WordPress can prevent hackers from easily identifying table names on your website.
Change security key
Update security keys in the wp-config.php file by replacing them with unique phrases. Obtain these phrases from a key generator link provided in the article.
Editing files in wp-admin
Prohibit editing files like plugins and themes in wp-admin by adding a code snippet to the wp-config.php file.
Install plugins and themes in wp-admin
Forbid the installation of plugins and themes in wp-admin by adding another code snippet to the wp-config.php file.
Chmod file wp-config.php
Set the permission of the wp-config.php file to 400 or 404 to enhance security.
Secure wp-config.php with .htaccess
Protect the wp-config.php file by adding specific code at the end of the .htaccess file.
Protect wp-content folder
Create a .htaccess file to protect the wp-content folder. Customize the code to include extensions related to WordPress source code files.
Lock wp-admin path
Block access to wp-admin directory and wp-login.php file by creating an .htaccess file with specific directives, allowing access only from your IP address.
Use malware scanning plugins
Utilize malware scanning plugins like Wordfence Scan, Anti-Malware, 6Scan Security, and Sucuri Premium to detect and remove malicious scripts from your host.
By implementing these security measures, you can effectively limit local attacks in WordPress and ensure the safety of your website. Additionally, choosing a reliable hosting provider that supports local attack restrictions is crucial for maintaining the security of your website.