WordPress users need to be aware of malware being inserted into their source code and database, which can lead to issues on their website. Malware can infect both the code and database, requiring immediate action to scan and clean them. There are two methods to do this – manually or using a plugin. Signs of malware infection in the database include malicious PHP functions and unknown links or iFrames. To clean the database manually, users must export the SQL database, identify and remove suspicious content, and verify the website’s functionality. Using plugins like MalCare WordPress Security or All in One WP Security & Firewall can also help detect malware effectively.
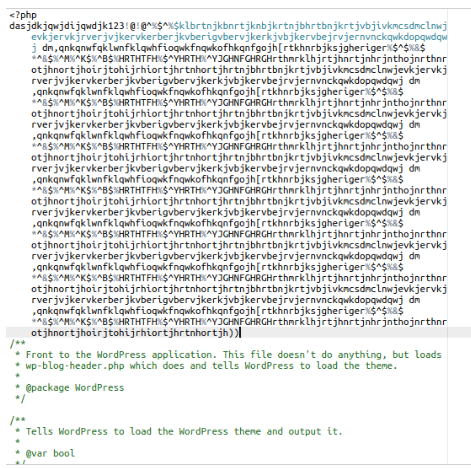
Having malware on your WordPress site can be a real pain. Not only do you need to clean up the code, but you might also find that the malware has infected your database as well.
If you suspect your database is compromised, it’s crucial to act fast. You can either manually scan and clean the database or use a plugin to help you out.
Before diving into the cleanup process, make sure to back up all your data and ensure that your source code is clean to prevent re-infection.
When it comes to manually scanning your database, keep an eye out for malicious PHP functions like base64_decode, gzinflate, error_reporting(0), and shell_exec. These functions are often used by hackers to inject malicious code.
To start the manual cleaning process, export your SQL database using Phpmyadmin or SSH. Look for suspicious content in the exported file and remove any malicious links, iFrames, or functions.
If you’re not comfortable with manual cleaning, using plugins like MalCare WordPress Security or All in One WP Security & Firewall can make the process easier and more effective.
By following these steps and using the right tools, you can effectively scan and clean your WordPress database, ensuring your site stays safe and secure.